Google Workspace vs. Microsoft 365 for ABA: A Complete Guide to Cost, Compliance, and Device Management
Oct 16, 2025
Applied Behavior Analysis (ABA) providers handle Protected Health Information (PHI) every day. That makes your choice of productivity platform more than a just a preference - it’s a risk decision that affects HIPAA compliance, total cost of ownership (TCO), and how efficiently you can onboard RBTs, BCBAs, and admins across systems, computers and mobile devices. Whether you’re using Google Workspace or Microsoft 365, it’s important to start viewing these platforms as far more than just tools for email and file storage. They should serve as the foundation of your IT infrastructure. It should be the central hub where identity, security, data, and device management all come together. By building your environment directly on a platform that you own and control, you ensure that your organization, not your IT provider, retains ownership of your systems and data.
When an outside IT company or your internal IT team builds your infrastructure entirely within their own ecosystem, it effectively locks you in. Transitioning to a new IT solution, like changing providers or bringing IT in-house later becomes a painful, time-consuming process, sometimes even impossible without major disruptions. We’ve even seen situations so extreme that companies had to get their attorneys involved to force their IT provider to release control of their data and systems. Instead, your goal should be to establish your IT environment inside your own Google Workspace or Microsoft 365 tenant and simply plug your IT team or vendor into it. That way, no matter who manages your IT (outsourced, internal, DIY) you maintain full control and continuity over your systems.
After working with hundreds of ABA organizations, our view is simple: both Google Workspace and Microsoft 365 can be configured for HIPAA compliance, but Microsoft 365 always provides a lower total cost, stronger device security, and a far more unified management experience especially across the mixed Mac and Windows environments that are common in ABA clinics. Microsoft’s built-in management tools cover both operating systems seamlessly, reducing the need for multiple third-party platforms and security vendors.
If you love Google’s interface enough to take on the extra cost and complexity, it can still be made to work. But for most ABA organizations looking to balance security, compliance, and simplicity, Microsoft 365 remains the clear, more cost-effective choice.
Below is the "why" - and the sources to back it up.
Before We Go Further: What Exactly Is Considered PHI, and What a BAA Does (and Doesn’t) Do

A Business Associate Agreement (BAA) is a contract required by HIPAA when a covered entity (your ABA practice) shares Protected Health Information (PHI) with a third party (a business associate) that will create, receive, maintain, or transmit that PHI on your behalf. Think cloud email and file platforms, EHR/practice management vendors, data collection systems, billing services, IT providers, marketing contractors who see client info, and even individual 1099 clinicians.
What is PHI?
Here’s the simplest, safest way to think about PHI… plus clear examples and who needs a BAA.
To be on the safe side, treat it as PHI if BOTH are true:
- It relates to health care (past, present, or future condition, care, or payment), and
- It identifies a person (directly or because it could reasonably identify them when combined with other info).
This applies to anything you hold as a covered entity or business associate whether in the form of email, web forms, spreadsheets, texts, voicemails, PDFs, or any other paper or electronic media that contains PHI.
Summary of the HIPAA Privacy Rule | HHS.gov
HHS also says data are not de-identified unless all 18 identifiers are removed (safe harbor) and you don’t actually know who it is. Identifiers include names, email, phone, addresses, dates (other than year), IP addresses, URLs, device IDs, photos, and “any other unique code/characteristic.” Initials and “last 4 of SSN” are not enough to qualify as de-identified.
Methods for De-identification of PHI | HHS.gov
Practical examples (assume PHI unless you’ve explicitly designed around it)
-
Website contact/intake form:
If the form asks (or the person writes) anything about diagnosis, therapy, symptoms, insurance, prior providers, medications, or scheduling care, then that submission is PHI. If a third-party form tool, website host, CRM, or email relay stores or transmits those entries, that vendor is a business associate and you need a BAA.
-
Emailing your practice:
An email from a parent like “My child (8) needs ABA; we have XYZ plan” is PHI once received by your practice. Email systems handling it (hosted mail, secure message gateway, archival/backup) are business associates and should be covered by a BAA; apply Security Rule safeguards (encryption/MFA, minimum necessary, etc.).
Does HIPAA permit health care providers to use e-mail to discuss with their patients | HHS.gov
-
Using initials (“J.S.”) instead of a name:
Not sufficient. HHS de-identification guidance explicitly notes that initials (like the last 4 of SSN) do not meet safe-harbor de-identification. If the context is about an identifiable person’s care/payment, treat it as PHI.
-
Anonymized website “general inquiry” form:
If the form only collects business contact info to request a demo (no health details) and you truly can’t infer a person’s care and your workflow keeps it that way, it likely isn’t PHI. The moment health details show up (even in a free-text box), it is PHI. When in doubt, assume PHI.
“Who needs a BAA?” (quick rule)
You need a BAA with any vendor that creates, receives, maintains, or transmits PHI for you such as email and file platforms, web form tools, EHR/PM, data collection, billing, backups/archives, texting platforms, IT providers with access, and 1099 contractors who handle PHI. (Employees are covered by your internal policies/training; 1099s are business associates.)
Covered Entities and Business Associates | HHS.gov
HHS provides model BAA language and a checklist of what BAAs must require (safeguards, breach notice, subcontractor flow-downs, return/destruction, termination rights).
Business Associate Contracts | HHS.gov
You. Are. Responsible. Period.
You are responsible for protecting PHI. BAAs don’t make you “HIPAA compliant” by themselves. You still need risk analysis, policies, training, and technical controls (MFA, encryption, MDM, logging, backups).
Design “PHI-aware” intake. If you accept health details by web form or email, put BAAs in place for every system in the path (form tool → site host → mail relay → inbox → archive/backup) or route people to a secure intake portal. If it helps, draw out your intake flow on paper or a white board, so that you can make sure that every step in the flow is secure and compliant.
When in doubt, treat it as PHI. If information is about care/payment and could reasonably identify someone (directly or indirectly), protect it and cover the vendors handling it.
To learn more about what a BAA is and is not, watch this webinar recording with ABA-specialized attorney, Samuel Bryant of Bryant Taylor Law (https://sbttlaw.com/):
Why a BAA Does NOT Make You HIPAA Compliant | Legal Insights for ABA Practices with Sam Bryant
As Sam emphasized in the webinar: you're required to obtain a BAA from all of your business associates, but it is not a golden ticket to HIPAA compliance. It defines the relationship regarding who must do what to safeguard PHI. You are still responsible for building and running a compliant program inside your practice.
Below is exactly how that works in the real world.
Roles & When a BAA Is Required
-
Covered entity (you).
ABA providers are covered entities whether or not you bill insurance. If you handle PHI, HIPAA applies.
-
Business associate (your vendor or contractor).
Anyone outside your W-2 workforce who can access PHI is a business associate and needs a signed BAA before they touch PHI.
-
Subcontractors.
If your vendor uses subcontractors who touch PHI, the vendor must flow down equivalent BAA obligations to them.
Common examples for ABA businesses:
-
Google/Microsoft, EHR, billing & RCM partners → BAA required
-
Fractional/contract BCBAs, consultants, c-suite or admin staff (1099) who handle PHI → BAA required
1099 contractors are not your “workforce” in HIPAA’s eyes. Treat them as business associates and use a BAA. Employees don’t need a BAA because you cover them under internal policies and training.
-
Marketing/CRM, call-answering, transcription, data analytics with any PHI exposure → BAA required
-
Purely de-identified analytics with no re-identification risk → May not require a BAA (confirm with your legal counsel and compliance officer)
What a BAA Does
A strong BAA typically:
-
Defines permitted uses/disclosures of PHI by the business associate.
-
Requires administrative, physical, and technical safeguards, including access controls, encryption, and secure transmission/storage.
-
Requires breach detection and notification to you within a defined time window, with cooperation on investigation and mitigation.
-
Imposes minimum necessary and subcontractor flow-down duties.
-
Requires return or destruction of PHI at termination (with exceptions if law requires retention).
-
Allows inspection/audit or documentation to demonstrate compliance.
-
Allocates responsibility for HIPAA documentation and record retention related to the BA’s services.
What a BAA Does Not Do (the big myths)
-
It does not make you HIPAA compliant.
Signing a vendor’s “HIPAA plan” or checking a “HIPAA version” box does not complete your compliance program. Sam was blunt about this: the “HIPAA-compliant software” pitch is extremely misleading.
-
It does not shift all liability away from you.
You remain responsible for your own program including risk assessments, policies, training, technical controls, and reporting.
-
It is not a certification.
HHS/OCR does not certify software or vendors as “HIPAA compliant.”
-
It is not your risk management program.
You still need periodic third-party risk assessments, remediation plan of action and milestones, staff training, and ongoing governance.
-
It is not a data-backup/continuity plan.
Vendors’ SLAs are not the same as your HIPAA-required data redundancy and recovery standards. You must ensure independent backup/retention that you control.
-
It does not guarantee correct configuration.
If your tenant, devices, or sharing policies are misconfigured, the BAA won’t save you.
Internal vs. External Use of BAAs (and why 1099s matter)
-
External BAAs: You ↔ third-party vendors/contractors. Mandatory when PHI is involved.
-
Internal controls: Employees (W-2) aren’t business associates. Cover them with policies, procedures, training, and device controls.
-
Contractors (1099s): Treat as business associates. Your BAA should bind them to your policies, require secure handling of PHI (including on their personal devices), and push consequences for violations (see clause ideas below).
Enforcement Reality: Why Documentation Matters
OCR (the enforcement arm) uses tiers based on culpability from “unknowing” to “willful neglect.” Per Sam:
-
If you can show risk assessments, policies, training logs, and reasonable safeguards, you’re far more likely to land in Tier 1–2 territory if something goes wrong.
-
Ignorance is not a defense. Failing to implement basic safeguards or to report a breach can push you toward higher tiers and bigger penalties, even if you didn’t know you needed them.
-
Timely breach reporting is mandatory. Trying to “avoid trouble” by not reporting is exactly how you create bigger trouble.
Under 45 CFR §160.404, penalties are divided into four tiers based on intent and corrective action:
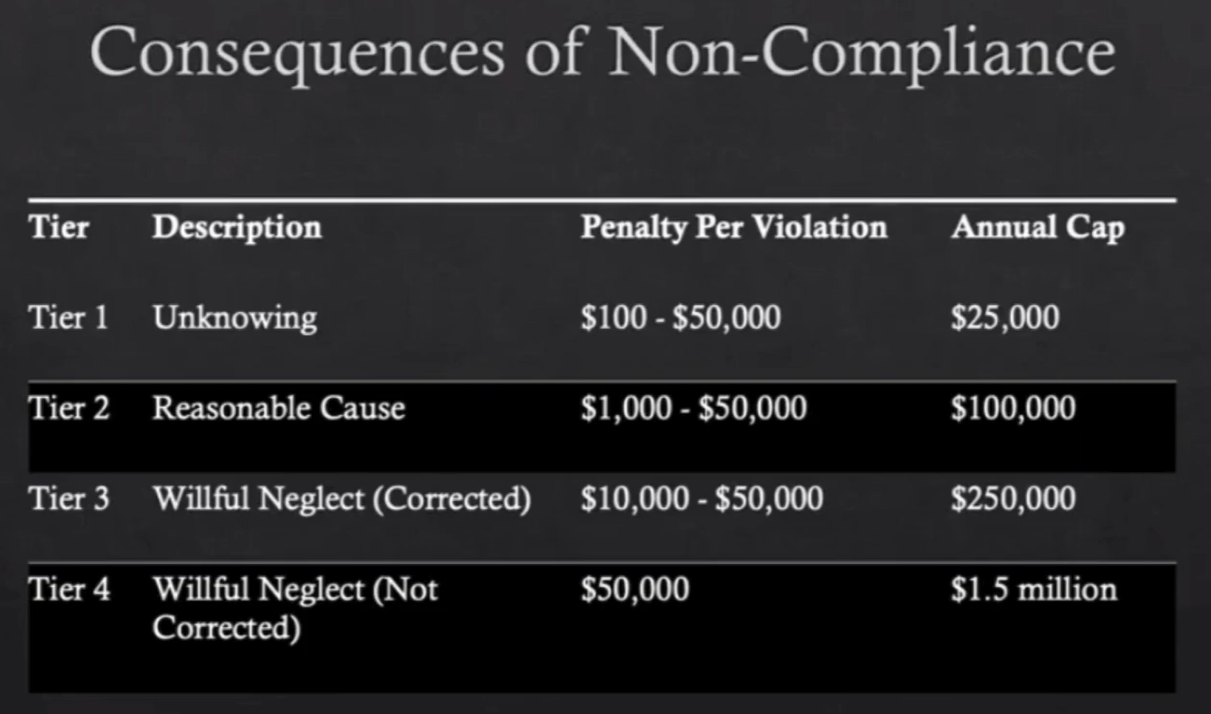
Source: 45 CFR 160.404 — Amount of a civil money penalty | eCFR
After You Sign a BAA: The Work That Actually Makes You Compliant
Sam’s “gym membership” analogy applies: the BAA is like when you sign up for your gym membership: you still have to work out.
- Risk analysis (and updates): Do a HIPAA risk assessment whenever your tech stack changes (new platform, new partner, new data flow), not just periodically.
- Policies & procedures: Access control, data sharing, email & texting PHI, device use (BYOD vs company-owned), removable media, backups/retention, incident response, sanctions.
- Training: Onboarding + periodic refreshers; role-based modules for clinical, admin, billing, and contractors.
- Technical safeguards: Identity (MFA), least-privilege access, encryption at rest/in transit, device management (Windows/macOS/iOS/Android), patching, EDR/AV, DLP, logging.
- Vendor oversight: Keep BAAs current, review SOC2/security docs where appropriate, confirm subcontractor flow-downs, and track breach-notification SLAs.
- Documentation: If it’s not written down, it didn’t happen. Keep risk assessments, policy versions, training rosters, incident logs, and vendor attestations.
Clause Ideas to Strengthen Your BAAs (especially for 1099s & niche vendors)
Work with counsel, but here are practical levers Sam discussed or implied:
-
Adherence to your policies: “BA will follow Covered Entity’s HIPAA policies/procedures and device standards.”
-
Security baseline: MFA required; encryption of devices and stored PHI; no shared accounts; patching cadence; prohibition on public Wi-Fi without VPN.
-
Breach clock: Notification within X hours of discovery; detailed incident report; cooperation and cost-sharing for mitigation when breach is BA-caused.
-
Subcontractors: Written approval + equivalent BAAs; BA remains responsible for subs.
-
Right to audit/assess: Reasonable audit rights or third-party attestations.
-
Return/Destruction: Upon termination, return PHI within X days and certify destruction of residual copies.
-
Indemnification: BA indemnifies you for losses caused by their negligence or noncompliance.
-
Insurance: Minimum cyber liability coverage amounts for BAs with meaningful PHI access.
-
Data ownership: Clear that you own the data; vendor has no lien; must provide export in usable format on request.
ABA-Specific Pitfalls (and how BAAs fit)
-
High contractor mix (1099s) → Use BAAs + strict device rules. Consider company-owned devices where feasible; otherwise require MDM enrollment for BYOD.
-
Schools, payors, multiple data flows → Map where PHI goes; ensure every external hop is under a BAA.
-
“HIPAA-compliant” software marketing → Treat as a red flag. Validate controls and ensure your program is in place.
-
Data redundancy → Don’t rely solely on vendor retention. Implement separate backups you control.
-
Transition risk (switching IT vendors) → Build on your tenant with your admin ownership; BAAs should guarantee data portability.
Getting back to Google Workspace vs M365…

Google Workspace: Google signs a BAA for listed Workspace/Cloud Identity services; you must execute that amendment and configure controls appropriately.
HIPAA Compliance with Google Workspace and Cloud Identity - Google Workspace Admin Help
Microsoft 365 (Direct): Microsoft provides a HIPAA BAA (via the Online Services DPA) for in-scope cloud services; as with Google, you still need proper security configuration.
As we’ve learned previously about BAAs, PHI, and who is responsible for protecting PHI, neither suite is “HIPAA compliant” out of the box. You sign the BAA and enable security controls either way. For HIPAA covered entities like ABA providers, the built-in breadth of Microsoft’s endpoint and identity stack usually reduces the add-ons you’ll need.
Understanding Microsoft Licensing: It’s Per User, Not Per Device
One of the most common misconceptions about Microsoft 365 is that licenses are assigned to computers or devices. In reality, Microsoft 365 licenses are per user, not per device. Each individual who needs to log in, access email, use their Microsoft 365 credentials for single sign-on (SSO) with other SaaS applications (such as practice management systems), use Office apps, or store files in OneDrive or SharePoint must have their own license. The specific type of license they need depends on the kind of devices they use... for example, full desktop access for computers, or lighter mobile-focused access for tablets and phones.
You should also avoid purchasing licenses for functional or shared accounts like billing@, admin@, or intake@. These don’t need their own licenses because Microsoft allows you to create shared mailboxes or aliases that can be linked to licensed users instead. Licenses are for individuals, not for departments or shared inboxes, and managing them this way helps you stay compliant, avoid unnecessary costs, and keep your environment organized.
Why Personal or External Company Emails Are a Security Risk
Allowing anyone, whether they’re an outside contractor, 1099 clinician, or internal employee to access your systems using a personal or external company email is one of the most serious HIPAA security risks an ABA organization can face. Every person who interacts with client data or PHI must use a company-managed credential that you control. This ensures you can enforce multi-factor authentication (MFA), apply security and device policies, monitor access, and revoke credentials immediately if needed.
When users log in with personal Gmail, Yahoo, or another company’s email domain, you lose visibility and control. You can’t guarantee encryption, device compliance, or proper offboarding when they leave. Even one unmanaged account can become a backdoor for a breach or a compliance violation. The safest, and only HIPAA-aligned approach is to issue company-owned Microsoft 365 or Google Workspace credentials for every individual with access to PHI, regardless of role or contract type.
Licensing, Scope, and Real-World TCO in ABA
Your licensing decision is not just about what tools you get. It’s about which platform becomes the backbone of your IT environment. In ABA settings, this decision touches email, identity, security, and device management all at once. Here's how the platforms stack up in actual operation (with the caveats you already know). Pricing changes and partner discounts happen; treat the numbers below as directional and check current lists before you buy - and here’s how we determine the right Microsoft 365 license based on each individual’s role and the type of device they use:
- Microsoft 365 Business Premium (for staff who use clinic computers, admin desktops/laptops, etc.): ~$25/user/month, includes full Intune device & app management, Defender for Business (AV/EDR), Azure AD (conditional access, identity protection), and the full Office suite. Microsoft 365 Business Plans and Pricing | Microsoft 365
- Microsoft 365 F3/Business Standard (for frontline / mobile-only staff like RBTs): ~$8/user/month, includes enough toolset plus Intune Plan 1 for endpoint/app controls, while excluding desktop Office apps (which frontline users often don’t need. Microsoft Intune Features | Microsoft Security
- Google Workspace (Enterprise tiers / advanced editions): ~$35/user/month Google’s enterprise plans bundle collaboration tools, email, and limited endpoint management features, but achieving full HIPAA compliance and security parity across your organization requires every user, regardless of their role or device type, to be on the same high-cost Enterprise license. Google’s model doesn’t allow you to mix and match license tiers based on function or need, meaning your administrative staff, mobile RBTs, and full-time clinicians all pay the same premium rate. To match Microsoft’s security posture on Google, you’d also need to layer on external MDM/UEM and endpoint security tools, adding even more cost, complexity, and vendor management overhead.
Because Microsoft bundles identity, security, and endpoint into one suite, many ABA providers find the “extra” cost of Google + third parties surpasses Microsoft’s baseline. In our experience, Google implementations that meet clinic-grade security often run 3–5× more expensive than implementations on M365 once you've added all necessary tools and services to meet compliance requirements.
Moreover, because Microsoft’s device, security, and identity layers integrate tightly, administration is unified. With Google, the baseline platform gives you only a slice of what you need, and each extra piece typically comes from a separate vendor, service and fees.
The decisive factor for ABA: Device management
In ABA, you’re often running Windows/macOS desktops & laptops for BCBAs, admin staff, or clinic PCs, plus iOS/Android or other mobile devices for RBTs in the field. Managing those endpoints - encryption, patching, app deploys, compliance, conditional access - is where the two ecosystems diverge sharply. Your ability to manage these from one console with unified policy, reporting, and compliance is crucial. Let’s compare how each platform handles it and where Google has gaps that force you to bolt on more tools.
What Google Workspace offers
Google’s Endpoint Management has tiers (Fundamental, Advanced, and Enterprise) and supports Android and iOS devices well, with limited Windows and macOS controls. Windows management depends on enabling Windows Device Management, optionally paired with Google Credential Provider for Windows (GCPW) for sign-in and enrollment.
In practice, Google’s Endpoint Management works best in environments that are 100% Google-native, for example, using Chromebooks and Google tablets. In those setups, management and security controls are more seamless because the hardware and operating system are fully integrated with Google’s ecosystem. However, that’s a very narrow use case. Most ABA organizations rely on a mix of Windows, macOS, and mobile devices, which Google’s platform doesn’t manage as comprehensively or efficiently.
For organizations running mixed-device environments or needing clinic-grade controls, Google’s model quickly becomes limiting. It lacks the flexibility and cost savings that Microsoft offers, where license tiers can be tailored by user role and device type. With Google, everyone must be on the same high-cost Enterprise tier to achieve full HIPAA compliance, something that’s both expensive and operationally inefficient. And while Google can technically manage Windows devices through GCPW, it’s far from the unified, real-time endpoint security and compliance management that Microsoft Intune provides natively.
(As for Chromebooks and Google hardware: why they’re not ideal for ABA is a whole separate conversation)
Here are some key points for why Google Workspace is not ideal for ABA:
-
Windows device management is off by default. You must explicitly enable it in Google Admin. Enable Windows device management - Google Workspace Admin Help
-
Google’s Windows management offers no deep system telemetry, no automatic patch orchestration, limited real-time hardware diagnostics, limited third-party app deployment, and no integrated EDR/advanced threat protection capability. Many IT admins describe it as “bolted on to account security rather than full endpoint security.”
-
Google’s Enhanced desktop security allows you to push sign-in settings (via Google Credential Provider for Windows, or GCPW) and some Windows settings, remote wipe, etc. Overview: Enhanced desktop security for Windows - Google Workspace Admin Help
-
For GCPW + Windows device management to work, you often enroll devices via GCPW such that signing in automatically triggers enrollment. Enroll a device in Windows device management - Google Workspace Admin Help
-
Many policies in Google’s Windows device management only apply after the device is enrolled, and some features are limited in scope. If policies aren’t syncing, devices may not receive your pushes. Google warns it may take hours for settings to take effect. Also, if a user’s license changes to one that does not support Windows management, the device may remain enrolled but will no longer receive future policies. FAQ for Windows device management - Google Workspace Admin Help
-
BitLocker policy settings are available - but policies “take effect if the device has BitLocker turned on” (nuance that matters if you expect zero-touch encryption enforcement). As a result, many organizations using Google for endpoint management still bring in a full UEM (commonly Microsoft Intune) to manage Windows more fully, leading to duplicate licensing complexity. For example, BitLocker will require you to have a M365 license in addition to your Google Workspace license. Configure BitLocker on Windows 10 or 11 devices - Google Workspace Admin Help
-
Feature availability depends on your Workspace edition; Windows device management sits in Advanced/Enterprise endpoint management tiers. Compare Google endpoint management feature sets - Google Workspace Admin Help
-
Some features (e.g. remote wipe) for Windows are limited or delayed. For example, remote wipe might not be fully supported in all cases. FAQ for Windows device management - Google Workspace Admin Help
-
Mobile (Android/iOS) can be managed agentless at a basic level; Advanced Mobile Management requires installing Google’s device policy app and additional setup. Endpoint Management and Security - Google Workspace
Google’s endpoint offering is strongest in mobile and lightweight device control but is not built for clinic-grade endpoint operations, especially in regulated settings. Google has steadily improved Windows controls (updates, BitLocker settings, local account permissions), but it’s not a full MDM/EDR stack. Many healthcare organizations still bolt on Microsoft Intune (or other UEM) for robust Windows compliance, app lifecycle, Conditional Access integration, Autopilot-style provisioning, and EDR adding cost and complexity on top of Workspace. (Even Google’s own guidance often pairs GCPW with Windows device management, and organizations frequently layer additional tools.) Enable Windows device management - Google Workspace Admin Help
Yes, you can run a Google-first shop, especially if your users adore the Gmail/Docs UI, but expect to purchase and integrate more tools to meet the same Windows security bar.
What Microsoft 365 includes (out of the box with Business Premium & F3)
- Microsoft Intune (Plan 1) for full device and app management across Windows, iOS/iPadOS, Android, and macOS built right into Business Premium and F3. Licenses available for Microsoft Intune - Microsoft Intune | Microsoft Learn
- Defender for Business (EDR/AV) with next-gen protection, firewall, web filtering, attack surface reduction, and endpoint detection/response policies are all manageable alongside Intune. Device protection in Microsoft 365 Business Premium - Microsoft 365 admin | Microsoft Learn
- Disk encryption, firewall, Defender AV, compliance: centrally deployable policies, baselines, and reporting from the Intune admin center. Device features and settings in Microsoft Intune - Microsoft Intune | Microsoft Learn
- Basic Mobility & Security exists in all M365 plans, but Business Premium elevates you to full Intune (what ABA teams actually need). Device and app management for your Microsoft 365 for enterprise tenants | Microsoft Learn
- Clinic-grade device management (BitLocker at first boot, autopilot provisioning, line-of-business app deployment, conditional access, compliance remediation, granular USB control, and integrated EDR) is native to Microsoft 365.
Microsoft 365 + Intune: built for full spectrum endpoint management
Microsoft’s endpoint solution, Intune (part of Microsoft Endpoint Manager), is purpose built to manage and secure devices at every layer. Because it's deeply integrated into the Microsoft ecosystem (Azure AD, Defender, security & compliance), it delivers a unified experience.
Key advantages:
- True cross-platform unified endpoint management: Windows, macOS, iOS, Android, even limited Linux support.
- Zero-touch provisioning / autopilot: New devices can ship direct to end users and automatically enroll, configure, install software, and enforce policies from first boot.
- Conditional Access + compliance gating: Devices must meet compliance rules (encryption, OS version, security posture) before accessing resources.
- Integrated AV/EDR via Defender for Business: No need for a third party antivirus - threat detection, remediation, firewall rules, threat protection, attack surface reduction all reside under Intune’s umbrella.
- Patch and update orchestration: You can manage update policies, delivery optimization rules, deferrals, feature update channels, and patching compliance across your fleet.
- App lifecycle management: Deploy Win32, MSI, EXE, MSIX, mobile apps, line-of-business apps - remotely install, update, uninstall.
- Granular device controls: USB restrictions, external storage enforcement, BitLocker encryption with escrow, hardware restrictions, local admin policy, conditional access, remote wipe / selective wipe.
- Comprehensive reporting & telemetry: Real-time device health, analytics, compliance dashboards.
- Role-based access & delegation: Let help desk, compliance, and security teams see only what they should.
- Built-in integration with Office 365, Teams, SharePoint, Conditional Access, Azure AD identity services - no stitching external systems.
Because Intune is included in Business Premium and F3, most ABA organizations get this full endpoint stack without needing to buy a separate UEM license. That means one console, one identity and policy framework, and fewer moving parts. In real usage, this unified stack significantly reduces the admin burden of connecting alerting, security, compliance, and app deployment across multiple vendors.
Scenario Comparisons: How things play out in ABA clinics
Here are concrete scenarios that many ABA providers see - and how Google and Microsoft differ.
Onboarding a Windows PC in clinic (fresh device)
- Microsoft 365 route: The device ships with Windows. The user turns it on, signs into Azure AD / Autopilot, Intune auto-enrolls, business policies push (BitLocker, security patches, required apps), compliance check is enforced before access to email or clinical systems.
- Google route: You’d need to enable Windows device management, deploy GCPW to devices, enroll them manually (or via scripted enrollment). Many policies may not apply until after enrollment. Some device control (patching, remote repair) may not be enforceable. Often you’ll supplement with Intune anyway – which means paying for a M365 license on top of your GW license.
Enforcing encryption, updates, and device compliance
- Microsoft: Intune can ensure BitLocker is enforced at first boot, escrow keys into Azure, enforce update rings and patch policies across devices, and mark devices noncompliant if missing patches or encryption.
- Google: Google allows some encryption policy enforcement but often only if BitLocker is already on, and it may lack mechanisms to force patch compliance or remediate automatically. Policies may lag or require manual user sync.
Field / mobile devices (RBTs)
- Microsoft: Via Intune and mobile app protection policies, you can control how works apps behave (app lock, data isolation, PIN requirements, conditional access), wipe corporate data if device is lost, and prevent noncompliant devices from accessing PHI systems.
- Google: Google’s mobile endpoint management is solid (especially Android), supports remote account wipe, device encryption enforcement, passcode policies, and app restrictions. But complex app protection and conditional access scenarios often require third-party tools or hybrid configuration.
Mixed OS (Mac + Windows + mobile) environments
- Microsoft: Intune supports macOS, so you can have one console managing your Mac admin machines, Windows clinic machines, and mobile devices. Policies can be coordinated, compliance status visible in one dashboard.
- Google: Mac management under Google is weaker because macOS support exists but lacks the rich control that Intune offers. To get clinic-grade macOS and Windows parity, you often bolt on a UEM with better macOS support, increasing complexity.
Real Risks & Hidden Costs in Google-centric setups
Vendor sprawl: To match Microsoft’s device/security features, you’ll almost always add third parties (MDM, EDR, patch manager, identity tools). That increases licensing, integration work, and support complexity.
License overlap: You may end up buying Microsoft Intune anyway even in a Google shop - so you pay for Google + Microsoft + whatever else you're layering. Why not consolidate?
Delayed enforcement & sync latency: Google may take hours to sync policies; delayed enforcement or device check-ins can open compliance gaps.
Weak troubleshooting & diagnostics: Google lacks deep hardware telemetry (CPU, memory, disk, failure rates) that Intune provides. That impairs proactive support and predictive maintenance.
License eligibility risk: If a user’s license doesn’t support device management, the device may no longer receive updates or new settings.
Lock-in risk reversed: If you built your IT environment inside your Google tenant but then need to migrate or switch, disentangling identity, devices, policies, and third-party dependencies is a heavy lift. This ties directly back to the tenant-ownership point we emphasized earlier.
To reach the security/compliance posture ABA clinics expect on Windows with Google, you typically add:
- An actual UEM/MDM for Windows (often Microsoft Intune anyway),
- Endpoint security/EDR,
- Sometimes identity/conditional access tooling to tie it together.
With Microsoft 365 Business Premium, those are already included, so your license consolidates: productivity + identity + device management + endpoint security. That’s why ABA orgs regularly see Google TCO run 3–5× higher after bolting on third-party tools to match M365’s baseline, even before the extra admin time for vendor wrangling.
A common gotcha: organizations start on Google for email/docs, then discover they still need Intune or other third-party non-Google tools to properly manage devices. At that point you’re paying for Google + Microsoft anyway plus the overhead of stitching them together with other third-party tools.
Next Steps: How to Make Sure Your Google Workspace or Microsoft 365 Is HIPAA Compliant
At ABA Impact, we offer some free or low-cost ways to evaluate, secure, and prove HIPAA compliance, no matter where you are in your journey. These are designed specifically for ABA practices that want to protect client data, reduce audit risk, and avoid expensive cleanup later.
Timing: Migrate Before PHI Flows
Whether you choose Google Workspace or Microsoft 365, it’s critical to finalize your BAAs and complete your security and device management setup before storing, transmitting, or receiving PHI. Doing this early prevents costly cleanup projects, audit exposure, and the pain of retrofitting security controls across already-active accounts and devices.
Safe, Free Migration (Under 5 Users – No PHI Yet)
If you’re still in the early stages of your startup and haven’t yet handled any PHI, you can migrate from Google Workspace to Microsoft 365 safely, and even for free, using Microsoft’s and Google’s built-in migration tools. For small organizations with fewer than five users, this manual migration is simple and cost-effective, if no PHI has been transmitted or stored in your Google environment yet.
Step 1: Create your Microsoft 365 tenant so you have somewhere to migrate your data using our free course: eBCBA Blueprint™: Foundation, that walks you through setting up your Microsoft 365 tenant for free.
- Sign up for the free Foundation course and create your M365 Tenant: https://ebcba.abaimpact.com/ebcba-blueprint-foundation
Step 2: Once you’ve completed that, our team will help you move everything, also for free.
- Book your free manual migration session: https://meetings.hubspot.com/derreck-ogden/google-workspace-to-m365-manual-transition
For Larger Teams or Those Who’ve Already Handled PHI
If your organization has more than five users, or you’ve already received, transmitted, or stored PHI in Google Workspace, we strongly advise against a DIY migration.
While it’s still technically possible to move data using free tools, doing so without proper backups, retention planning, and migration validation carries serious risks, especially around data loss and record-retention compliance. Losing even a single therapy note, email, or file that contains PHI can constitute a HIPAA violation.
The safe approach is to perform a structured, professional migration that includes full data verification, secure backups, and proper record retention before deactivating your old workspace.
If this describes your situation, we recommend starting with a Free Google Workspace or Microsoft 365 Compliance Assessment. This assessment includes a no-cost consultation where we’ll:
- Review your current environment,
- Estimate the cost and scope of a professional migration, and
- Provide tailored recommendations for securing and optimizing your environment moving forward.
See the Free Google Workspace or Microsoft 365 Compliance Assessment section for details and the booking link.
Why You Should Never Buy Microsoft 365 Through GoDaddy (or any other reseller)
If you’re setting up Microsoft 365 for your ABA organization, do not purchase your licenses through GoDaddy or any other reseller. Only buy directly from Microsoft. Here’s why:
You Don’t Control Your Own Tenant.
When you purchase Microsoft 365 from GoDaddy, they automatically insert a Global Administrator account into your environment. This hidden admin account overrides your permissions and allows GoDaddy to make changes to your settings at any time, without your approval or even your knowledge.
GoDaddy has a long and well-documented history of security breaches, and when their systems are compromised, those attackers can use the GoDaddy Global Admin account to gain access to your Microsoft 365 tenant and, by extension, your clients’ PHI.
That creates a direct HIPAA violation: you now have an external, unauthorized entity with technical access to PHI, on an account you don’t control, can’t secure with Multi-Factor Authentication (MFA), and can’t even reset the password for.
You Can’t Enforce HIPAA Security Requirements.
GoDaddy’s version of Microsoft 365 disables or restricts key enterprise security features like Conditional Access, MFA enforcement, and audit log visibility. These are not optional settings under HIPAA, they’re mandatory safeguards for controlling access, monitoring data use, and preventing unauthorized disclosures. Even if you have a Business Associate Agreement (BAA) in place, your environment will still be noncompliant by design.
Your Data Is at Risk.
The Federal Trade Commission (FTC) has filed formal complaints against GoDaddy for poor security practices that exposed thousands of business accounts to cyberattacks. If your tenant is hosted through GoDaddy, you’re inheriting those vulnerabilities and exposing your clients’ protected data to unnecessary risk.
You Can’t Produce Required Audit Logs.
HIPAA’s Security Rule requires covered entities and business associates to maintain detailed audit trails showing who accessed PHI, when they accessed it, and from where. However, GoDaddy’s version of Microsoft 365 restricts or completely blocks access to many of the built-in logging and reporting tools needed to meet this requirement. As a result, if your organization is ever audited or experiences a breach, you may be unable to produce the records necessary to prove compliance. Even worse, it can dramatically increase the cost and complexity of data forensics and incident response, since it takes longer to determine how the breach occurred, what data was exposed, and who must be notified.
You Can’t Fully Secure Your Environment.
Because GoDaddy retains system-level control over your Microsoft 365 tenant, you lose access to many of the built-in enterprise-grade security tools that normally come with standard Microsoft licensing. Features like Microsoft Defender for Business, Data Loss Prevention (DLP), Endpoint Compliance policies, and Conditional Access aren’t fully available or manageable in the GoDaddy environment. While it’s technically possible to achieve similar protections using third-party tools, doing so adds cost, complexity, and additional vendors to manage. More importantly, it fragments your security stack, making it harder to enforce encryption, detect malware, and prevent unauthorized data sharing, all of which are essential to meeting HIPAA’s Technical Safeguards.
How to Fix It (Defederation)
If you’ve already set up Microsoft 365 through GoDaddy, don’t panic, but don’t ignore it either.
You’ll need to defederate your environment, which means breaking GoDaddy’s control and reestablishing direct ownership with Microsoft.
We offer two ways to do this safely:
- DIY Defederation Guide: A free step-by-step manual that walks you through the process carefully, including how to avoid lockouts and data loss.
- Defederation-as-a-Service: Our experts perform the migration for you, ensuring you don’t lose access, break integrations, or risk PHI exposure.
You can request the DIY guide or an expert defederation quote during your Free Google Workspace or Microsoft 365 Compliance Assessment where we’ll review your current setup, identify risks, and help you plan a safe path forward.
See the Free Google Workspace or Microsoft 365 Compliance Assessment section for details and the booking link.
Free Google Workspace or Microsoft 365 Compliance Assessment
If you’re not sure where your organization stands today, we offer a Free Google Workspace or Microsoft 365 Compliance Assessment to help you identify security or compliance gaps before they become problems.
During this review, our team will:
- Audit your environment (Google Admin or Microsoft 365) to evaluate key areas like account security, device management, data loss prevention, and HIPAA configurations.
- Check your licensing alignment to ensure you’re not under- or over-licensed for compliance.
- Identify critical risks such as unsecured sharing, unmanaged devices, missing encryption policies, or unprotected PHI storage.
- Make real-time improvements during the call where possible, closing easy gaps immediately.
- Provide recommendations for tightening your environment’s security and meeting HIPAA and security standards.
This free assessment will help you understand where you stand, fix what you can now, and create a clear path toward full compliance, whether you stay on Google or transition to Microsoft.
Schedule your free assessment: https://meetings.hubspot.com/joshnelson/free-15-minute-compliance-consult
Want to Dive Deeper? Introducing ABA Impact’s Audit Readiness Jumpstart
ABA Impact’s Audit Readiness Jumpstart (ARJ) is a fast-track, high-impact private engagement built to eliminate compliance blind spots across your organization’s infrastructure, documentation, and security posture.
This isn’t just a course or a one-size-fits-all checklist, it’s a done-with-you, expert-led sprint designed specifically for ABA providers who want to become compliant, audit-ready, and operationally stable without wasting months or tens of thousands of dollars.
Whether you’re a solo BCBA, a growing team, or a multi-site organization, we tailor every part of the engagement to your actual environment, including your Google Workspace or Microsoft 365 setup, devices, policies, and PHI workflows.
What’s Included:
Our Audit Readiness Assessment combines an abbreviated HIPAA Security Risk Assessment (SRA), a technical vulnerability scan (penetration test), and an enterprise-grade email security evaluation, all aligned with HHS and NIST frameworks.
Normally valued at $14,000+, ABA providers can access it for just $997 through our community program – and if you keep reading, you’ll learn how you can actually get this ARJ for FREE.
Why We Offer Such a Deep Discount for ABA Therapy Providers:
ABA isn’t our only market, but it’s the one closest to our hearts. Our founder, Derreck Ogden, has two nephews on the autism spectrum who’ve both experienced what happens when therapy is delayed or inaccessible, as well as how it impacted their families. That experience drives our mission to help ABA organizations succeed, not struggle.
We know that many ABA startups fail early, (about 10% of ABA businesses fail within their first year) not because of poor clinical quality, but because they face overwhelming technology, compliance, and security barriers before they even get a chance to grow. The Audit Readiness Jumpstart and our community pricing exist to change that.
By offering enterprise-grade cybersecurity and compliance services at a fraction of their market cost, we’re making it possible for more ABA founders to start strong, stay compliant, and scale safely. We believe the world needs more ABA providers, and this is our way of helping to make that happen. This is our contribution to the field as non-clinicians.
Here’s what’s included in the Audit Readiness Jumpstart:
- 20-Point Compliance & Security Inspection
A comprehensive review of administrative, physical, and technical safeguards across your environment, covering device encryption, MFA, data loss prevention, backups, and access controls. - Plan of Action & Milestones (POAM)
A documented, plain-English roadmap showing where you are now, what’s missing, and how to close the gaps, prioritized by impact, cost, and compliance requirement. - Corrective Action Roadmap & Tracker (CART)
Your interactive plan for executing improvements, assigning responsibilities, and tracking progress over time. - Real-World Threat Simulation & Tabletop Exercises
We run practical attack simulations, including phishing and ransomware, to show how your systems respond and where your staff need extra protection or training. - Email Security & Device Hardening Workshop
A live, hands-on session for Google Workspace or Microsoft 365 users where we help you configure or enhance your existing tools for free, no extra software required. - Partner-Focused Compliance Summary
A one-page compliance and risk summary aligned to HIPAA, payer, state, and accreditation requirements, so you can easily demonstrate audit readiness to stakeholders, partners, or insurers.
This assessment doesn’t just identify problems... it gives you the tools, documentation, and confidence to fix them.
The Audit Readiness Jumpstart Process
- Kickoff Discovery Session (45-60 min)
A guided walkthrough of your real-world environment to uncover vulnerabilities, missing controls, and areas of exposure. Includes a HIPAA SRA (abbreviated, HHS-aligned), system audit, and live vulnerability mapping. - Analysis & Strategic Planning (We Do the Heavy Lifting)
Our team handles the technical analysis and documentation design. You’ll receive a POAM and CART, customized to your risks, budget, and timeline. - Executive Review & Strategy Call (90–120 min)
We walk you through your risks, corrective actions, and implementation strategy in plain English, ensuring you know what to prioritize and how to move forward. - Access to the ABA Founders’ Program
After your kickoff session, you’ll get started in our ABA Founders’ Program which is our implementation system for ABA providers that includes: - The free Foundation Course to stabilize your infrastructure, policies, and systems
- Executive Assistant GPT, your built-in AI compliance and documentation assistant
- Weekly Founders’ Calls for live support and workshops
- A free 1:1 business strategy call focused on scalability and growth
- The Fast Track Policy Builder
Using your Executive Assistant GPT and guided templates, you’ll develop your legally required Written Information Security Program (WISP) and HIPAA policies that will be audit-ready and mapped to OCR expectations. - Final Policy Review & Feedback Session
We review your entire policy library and make final adjustments before formal adoption, ensuring it meets both HIPAA and payer standards.
Why It Works
You don’t need a $45,000 consultant or an internal compliance officer.
You need a structured, supported system built specifically for ABA.
The Audit Readiness Jumpstart gives you the clarity, documentation, and protection you need to grow confidently, without adding unnecessary workload or tech bloat.
We’ve helped ABA owners go from disorganized Google Drives and unmanaged devices to full audit readiness in just a few weeks.
How to Access the Assessment for Free
You can access the Audit Readiness Assessment 100% free through either of the following options:
Option 1: Join the eBCBA Odyssey Program
Best for ABA founders who want full support, policy development, and long-term strategy.
- $97/month (30-day money-back guarantee)
- Includes full audit readiness training, policy creation tools, NIST OSCAL mapping, organizational structure strategy, and weekly calls with other ABA founders and industry experts.
- Audit Readiness Jumpstart (ARJ) included at no extra cost.
- Cloud Shield onboarding fee waived (normally $697).
Odyssey gives you everything you need to establish a compliant, scalable foundation.
Option 2: Subscribe to Cloud Shield
Best for ABA providers who already have a solid foundation and want to secure email and data immediately.
- $14.70/month per user
- $697 one-time onboarding fee (waived for Odyssey members)
Cloud Shield is one of the most effective ways to close multiple high-risk compliance gaps immediately for both Google Workspace and Microsoft 365 environments.
It automates core HIPAA Security Rule safeguards and generates audit-ready documentation.
What’s Included in Cloud Shield:
|
Feature |
Benefit |
HIPAA Citation |
|
Automated Email Encryption |
Protects PHI in transit |
§164.312(e)(1), §164.312(a)(2)(iv) |
|
Advanced Spam Filtering |
Blocks phishing & malware |
§164.308(a)(5)(ii)(B) |
|
Attachment Sandboxing & Filtering |
Stops malicious files |
§164.308(a)(5)(ii)(B) |
|
Predictive URL Defense & Warning Tags |
Prevents credential theft |
§164.308(a)(5)(ii)(B) |
|
Real-Time Backup for M365/Google Email, OneDrive, Teams, SharePoint |
Ensures PHI recoverability |
§164.308(a)(7)(ii)(A)–(B) |
|
Encrypted, Secure Storage |
Protects backed-up PHI |
§164.312(a)(2)(iv), §164.312(c)(1) |
|
Granular, Point-in-Time Restore |
Enables precise recovery |
§164.308(a)(7)(ii)(B) |
|
Business Continuity & Retention |
Maintains readiness & record retention |
§164.308(a)(7)(ii)(C), §164.316(b)(1) |
Why It Matters
- Prevents 99% of data breaches and phishing attacks before they occur.
- Provides audit-ready logs, encryption, and backups.
- Demonstrates “good faith effort” to regulators and insurers.
- Reduces potential fines and reputation risk.
Every Cloud Shield subscription includes an Audit Readiness Jumpstart at no extra charge as part of the onboarding process.
Which option is right for you?
If you want to build full audit readiness program including policies, risk assessments, and compliance strategy, start with Odyssey.
https://ebcba.abaimpact.com/ebcba-odyssey-launch
If you already have that foundation and simply need to harden your email and data protection, start with Cloud Shield.
https://meetings.hubspot.com/joshnelson/cloud-shield-hipaa-sra-explained
Either path gets you the Audit Readiness Assessment free and moves your organization from Tier 4 → Tier 1 by showing evidence of active risk management, corrective action, and documented compliance efforts. The Audit Readiness Jumpstart and Cloud Shield deployment provide exactly that: proof that you’re engaged, improving, and not neglecting your responsibilities.
Click here to join the eBCBA™ Odyssey and reclaim your role as the visionary leader you’re meant to be.
Stay connected with news and updates!
Join our mailing list to receive the latest news and updates from our team.
Don't worry, your information will not be shared.
We hate SPAM. We will never sell your information, for any reason.